Here’s Part 1 if you missed it.
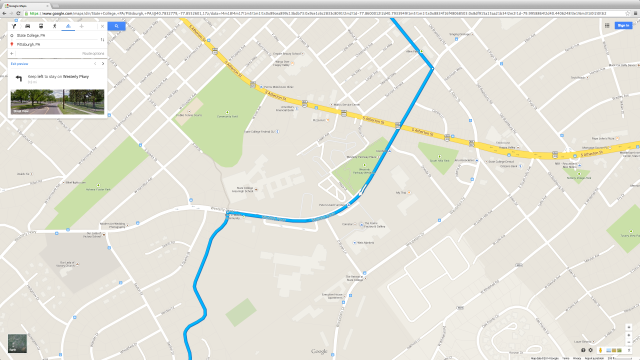
13. Turn right onto the Lower Trail
(Estimated) Time: 8:05 a.m.
Time from start (5:49 a.m.): 2 hours 16 minutes
Miles this step: 12.8
Miles total: 39.2
Comments: Picture!
The Lower Trail may be the finest piece of land I’ve had the pleasure of crossing. As the map shows it travels along the Juniata River; what it doesn’t show is the flush shades of green, nature’s panorama of the color ‘tween yellow and blue in all its glory and different hues. Aye, the eye marvels.
Besides that, it was nice to see this area in late spring after having seen its orange side in the fall. Maybe one day when we’ve solved the world’s more pressing situations we could let our cities’ buildings change color with the season. Imagine Manhattan’s skyline a egg blue in the srping, a soft green in summer, hard bronze in fall and pitch navy in winter. I’d be more inclined to visit, wouldn’t you?
I also saw a really intensely blue bird and stopped on a dime to take its picture. Alas, my attempt proved less than successful:
“O flighted one, thine color escapes my len’s net.” I have failed the birdwatchers of past and present.
The Lower Trail sparks a certain heightened rhetoric in all who pass through it; that’s the only explanation for why I’m keeping this verbal charade up. Next.
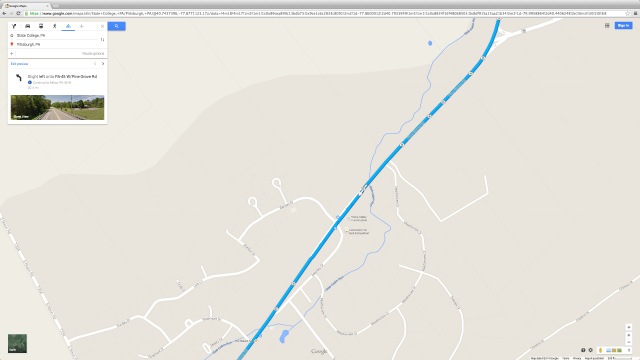
- Slight left on to stay on the Lower Trail
Time: 9:28 a.m.
Time from start: 3 hours 39 minutes
Miles this step: 3.5
Miles total: 42.7
Comments: Oh right, trails are long. I stopped at a gas station mart and ransacked their peanut butter cracker and Nutri-grain bar stock, only after locking myself in their bathroom and downing two bottles of tap water. A truck labeled Duncansville pulled into the parking lot as I sat on a picnic table eating. I wondered if I should ask anyone where I was. But I just kept going instead. Why, yes, I am a male.
- Continue onto Long Rd (220 ft)
- Continue straight onto T444 (0.2 miles)
- Turn left onto Flowing Spring Rd/T444 (486 ft)
- Turn left onto US-22 W
Time: 9:58 a.m.
Time from start: 4 hours 9 minutes
Miles this step: 0.6 + 0.2 + 706 ft (round down to 0.1) = 0.9
Miles total: 43.6
Comments: Amnesia strikes again! I don’t really remember these few steps. Probably because Google split less than a mile’s distance into four parts so my brain decided to package it as one big IDGAF.
19. Turn onto State Rte 1011
Time: 10:01 a.m.
Time from start: 4 hours 12 minutes
Miles this step: 1.2
Miles total: 44.8
Comments: It started to get hot around now. Hell begins outside Canoe Creek State Park (in an environmental sense).
- Turn left onto Turkey Valley Rd
Time: 10:13 a.m.
Time from start: 4 hours 24 minutes
Miles this step: 3.1
Miles total: 47.9
Comments: (Homer Simpson’s post-Satisfying Laugh voice) Turkey Valley Road.
At this point my technological will came to heads with my historical perspective/visceral preferring/present moment mind-state occupying will. (The initial verbal carnage set a bloody tone to the entire affair.) I was biking up this turkey road, passing lovely farms and lovelier horses; the sun had reached a respectable height; the valley lay below me like a waiting whore armchair seeming to cry for (photo)graphic embrace. It would be so seductively easy to whip out my phone and snap a picture of the miles-long landscape, upload it to Instagram – obviously shared to Facebook and Twitter – along with some kind of humblebraggy/overly self-depricating caption like “It was inevitable I’d end up having no clue where I am #happyvalley #psu #summer2014” etc., hinting to what followers I have that “Hey, I’m out and about like a bigshot cyclist guy and I’ve biked so far that I had to let you all know how awesome I am because that’s what you’re supposed to do in today’s world, right? Showcase those life events like a boss who manages the Humility Resources department (because God help you if it’s overt braggadocio – unless you go that route with no exceptions, then you might strike gold), and bask in the navel-gazing security of pending notifications.
But on the other side, the side I consider to have all the good qualities, like healthy self-esteem, reduced levels of neuroses, self-awareness and perspective on a variety situations, and a willingness to remain focused when the moment calls for it, that side would say, “What is the ephemeral pleasure of harvesting Likes when compared to appreciating the eternity-spanning instant of you on this mountainside and connected to the landscape, you as a part of the whole and simply playing your role for whatever reason that may be?” This side often goes “deep” and can be hard to understand, but I have years and years to try and understand it.
Compromise: no shallow Instagramming, just a picture of hope.
…so I guess the tech side won. [1]
21. Turn right onto US-22 W
Time: 10:13 a.m. (re-adjusted based on evidence)
Time from start: 4 hours 24 minutes
Miles this step: 6.0
Miles total: 53.9
Comments: The time stamp should be more accurate on this step, since I had to stop at a gas station convenience store and refuel on crackers. I ate those in the shade and called Penn State’s Media Tech department to renew the camera I’d checked out. My phone’s call log says I made that call at 10:31, maybe 6 minutes after I stopped there. That store stands about 12 minutes after this step starts, thus 10:13 a.m. makes sense as when I most likely began this step.
First sighting of a “This is Steelers country” flag on a porch. Oh ya.
Biking along 22 took me through Hollidaysburg and Duncansville, the latter of which has big shipping rail yard running through the center of town. It’s a smaller town (population of about 1,200), but it seems to export huge amounts of coal. Anecdotally, I thought the noise must be hard on the residents across the street.
Saw another cyclist at one intersection and for once I felt sure I was pulling the longer trek.
- Continue onto Old Rte 22
- Turn left onto Foot of Ten Rd
Time: 10:53 a.m.
Time from start: 5 hours 4 minutes
Miles this step: 2.0 + 0.2 = 2.2
Miles total: 56.1
Comments: After Turkey Valley, this gets my vote for best road name. It sounds so solid, like a Doric pillar.
- Turn left onto Valley Forge Rd
Time: 11:07 a.m.
Time from start: 5 hours 18 minutes
Miles this step: 0.6
Miles total: 56.7
Comments: A water break fit naturally here, since I had to stop anyway to take this picture:
There’s two possible explanations here. One, I stumbled on a portal showing some time in the future, far enough ahead that the nuclear wasteland had recovered and nature was again thriving but human wreckage had not entirely decayed, leaving traces like these for the posterity of future species to be. Or two, some kids played a prank on their bus driver who just snapped.

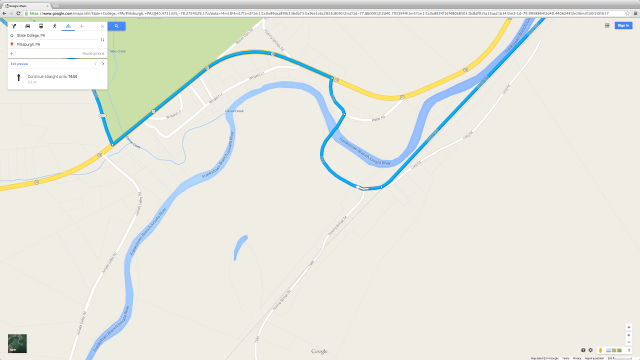
25. Turn right onto 6 to 10 trail (APRR)
Time: 11:17 a.m.
Time from start: 5 hours 28 minutes
Miles this step: 2.5
Miles total: 59.2
Comments:

I stopped around here to take this picture. I do not know what animal the bones belong to, or how it got this way. I was not keen on finding out, especially if the one responsible was nearby. And I needed to keep moving; fewer pictures and more pedaling, I told myself.
Of course, right before the end of the trail I came upon some construction, which lets me make the joke about thinking I had left State College to get away from all the construction. (It makes sense if you’ve lived there.) So, camera out while I walked my bike through the ROAD WORK AHEAD.
- Turn left onto Old Rte 22 [2]
Time: 11:32 a.m.
Time from start: 5 hours 43 minutes
Miles this step: 2.0
Miles total: 61.2
Comments: Holy crapping effing monkey jumping cheese balls, this was the worst step of the trip to this point. It was here that my now veteran hatred for Route 22 took its first halting but soon to be burgeoning steps, which incidentally is how I approached the uphill 2 miles here. Walking made me realize how little I would be able to do if someone driving by decided to abduct me. The highway system is not set up well for long individual commutes on non-motor vehicles.
Halfway up I rested outside the gated driveway of a somewhat randomly placed mansion and ate the rest of my crackers. My map told me there was a town coming up fairly soon, so I was more worried about the fact that I didn’t have more than a third of a Gatorade bottle’s water. I won’t lie: the main reason I didn’t turn around here was because I remembered that joke about blondes (a popular joke topic when I was in elementary school). One version of it goes like this:
“On a deserted island there were three women, a blonde, a brunette, and a redhead. They needed to get back to the mainland and the only way was by swimming. The redhead goes first. She makes it a quarter of the way and then she drowns. The brunette goes second, and makes it one third of the way before drowning. The blonde starts her swim last. She makes it half way and gets tired, so she swims all the way back to the island.”
I didn’t want to be the blonde.
Next time: Approaching Ebensburg, AKA The Summit Is Too Damn High!
Notes
[1] To learn more about therapeutic horseback riding, read here. The homepage for the one in the picture is here.
[2] I don’t know what’s going on with these headings. The HTML says they’re fine but then they don’t show up as the right numbers so that’s not fine. I’m going to not worry about it right now and maybe come back to it later if it seems to be distracting to reading.


















![\text{NOT }x = \sum_{n=0}^{b}2^n\left[\left(\left\lfloor\frac{x}{2^n}\right\rfloor \bmod 2 + 1\right) \bmod 2\right]](https://i0.wp.com/upload.wikimedia.org/math/c/7/1/c7135a98d0bec175f662de60e85b98c0.png)

![x\text{ OR }y = \sum_{n=0}^{b}2^n\left[\left[\left(\left\lfloor\frac{x}{2^n}\right\rfloor \bmod 2\right) + \left(\left\lfloor\frac{y}{2^n}\right\rfloor \bmod 2\right) + \left(\left\lfloor\frac{x}{2^n}\right\rfloor \bmod 2\right)\left(\left\lfloor\frac{y}{2^n}\right\rfloor \bmod 2\right)\bmod 2\right]\bmod 2\right]](https://i0.wp.com/upload.wikimedia.org/math/b/4/4/b44b329c5c1274f7f6ab0cec1e763a53.png)
![x\text{ XOR }y = \sum_{n=0}^{b}2^n\left[\left[\left(\left\lfloor\frac{x}{2^n}\right\rfloor \bmod 2\right) + \left(\left\lfloor\frac{y}{2^n}\right\rfloor \bmod 2\right)\right]\bmod 2\right]](https://i0.wp.com/upload.wikimedia.org/math/f/e/f/feff3247ae7fb3653f87c83cc63d42d1.png)
 is the number of bits in
is the number of bits in  for all
for all  .
.